Amazon.fr - Extreme Exploits: Advanced Defenses Against Hardcore Hacks (Hacking Exposed) - Friedrichs, Oliver, Oppleman, Victor, Watson, Brett - Livres
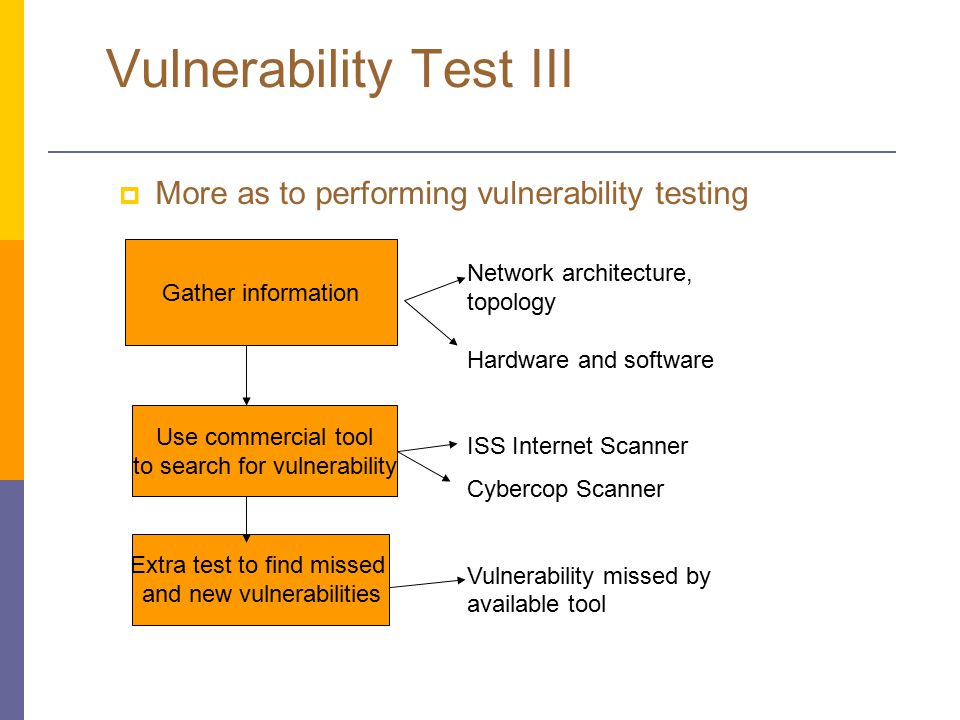
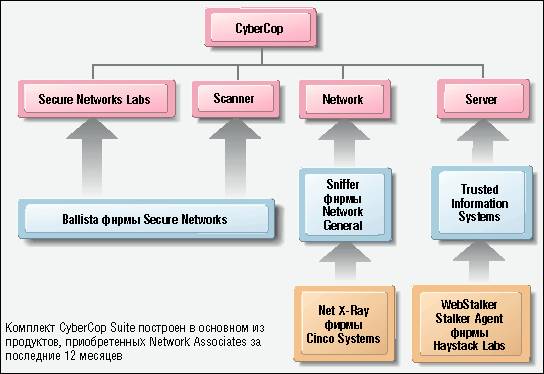
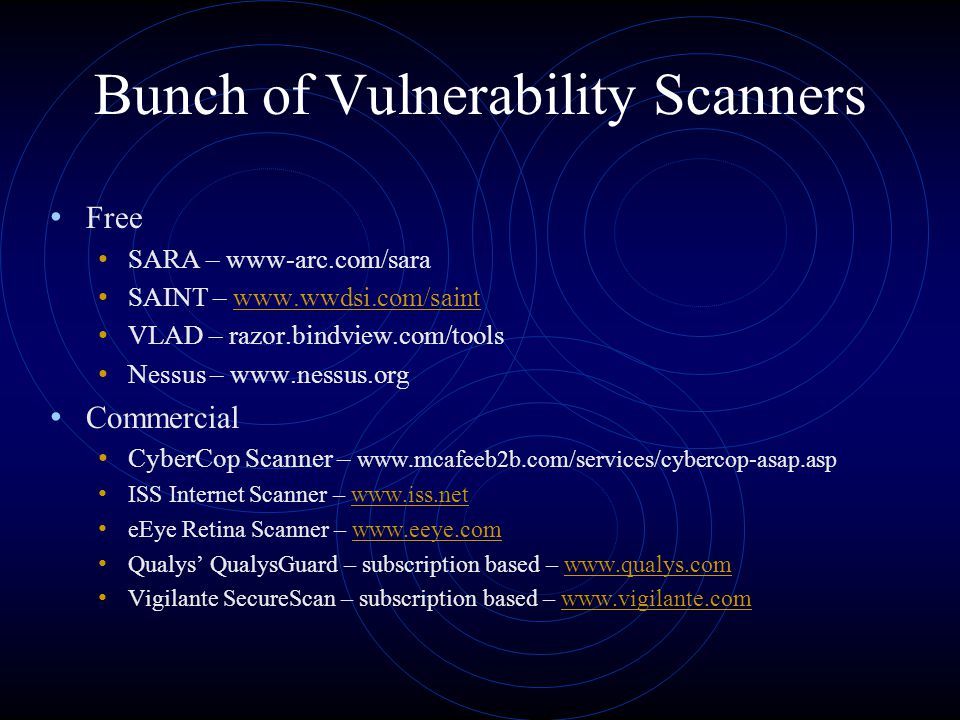
Comp 8130 Presentation Security Testing Group Members: U Hui Chen U Ming Chen U Xiaobin Wang. - ppt download

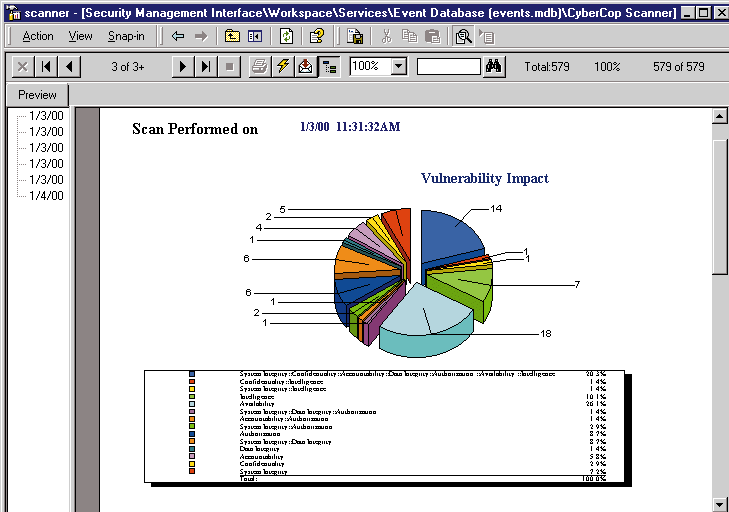
Cybercop Scanner Download: How to Scan Your Network for Vulnerabilities | Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ
BUY ONLINE AT: http://www.itgovernance.co.uk/products/946 HACK ATTACKS TESTING: HOW TO CONDUCT YOUR OWN SECURITY AUDIT

Amazon.fr - Extreme Exploits: Advanced Defenses Against Hardcore Hacks (Hacking Exposed) - Friedrichs, Oliver, Oppleman, Victor, Watson, Brett - Livres

![Cybercop Mercury - 3D model by wannaqiuddin (@wannaqiuddin) [b12cb1a] Cybercop Mercury - 3D model by wannaqiuddin (@wannaqiuddin) [b12cb1a]](https://media.sketchfab.com/models/b12cb1a64bb54895a564d138c3696415/thumbnails/474affa7f7a34c96b2b7d0a4db790934/ab0cc552a731483cab8a1d5f25ef6f6d.jpeg)