IOT Vulnerability Assessment using Raspberry Pi2 - Cyber Security Blogs - IoT Security - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata

Internet of things (IoT) and common vulnerability scoring system (CVSS) | Download Scientific Diagram
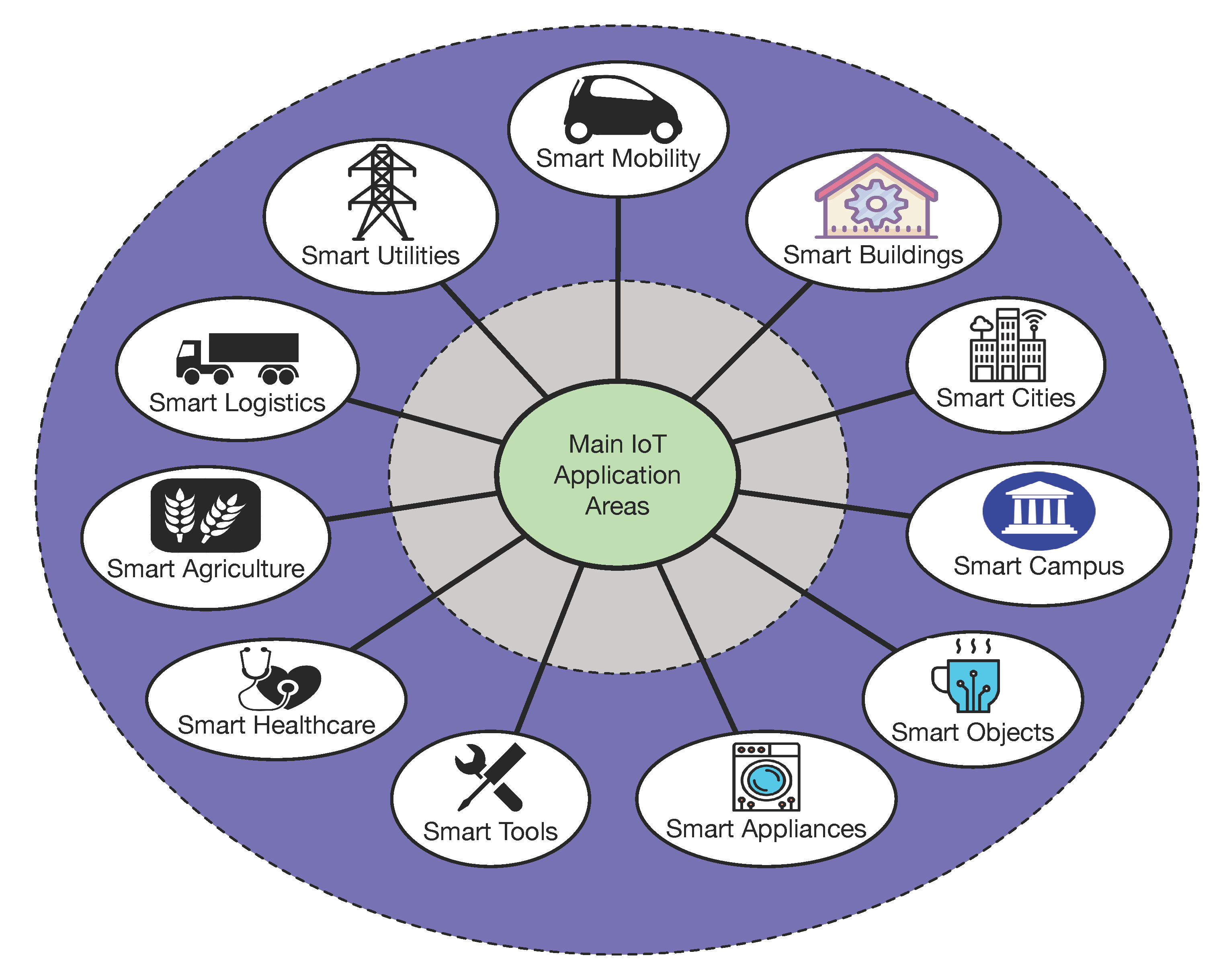
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

Introducing security for unmanaged devices in the Enterprise network with Microsoft Defender for IoT | Microsoft Security Blog
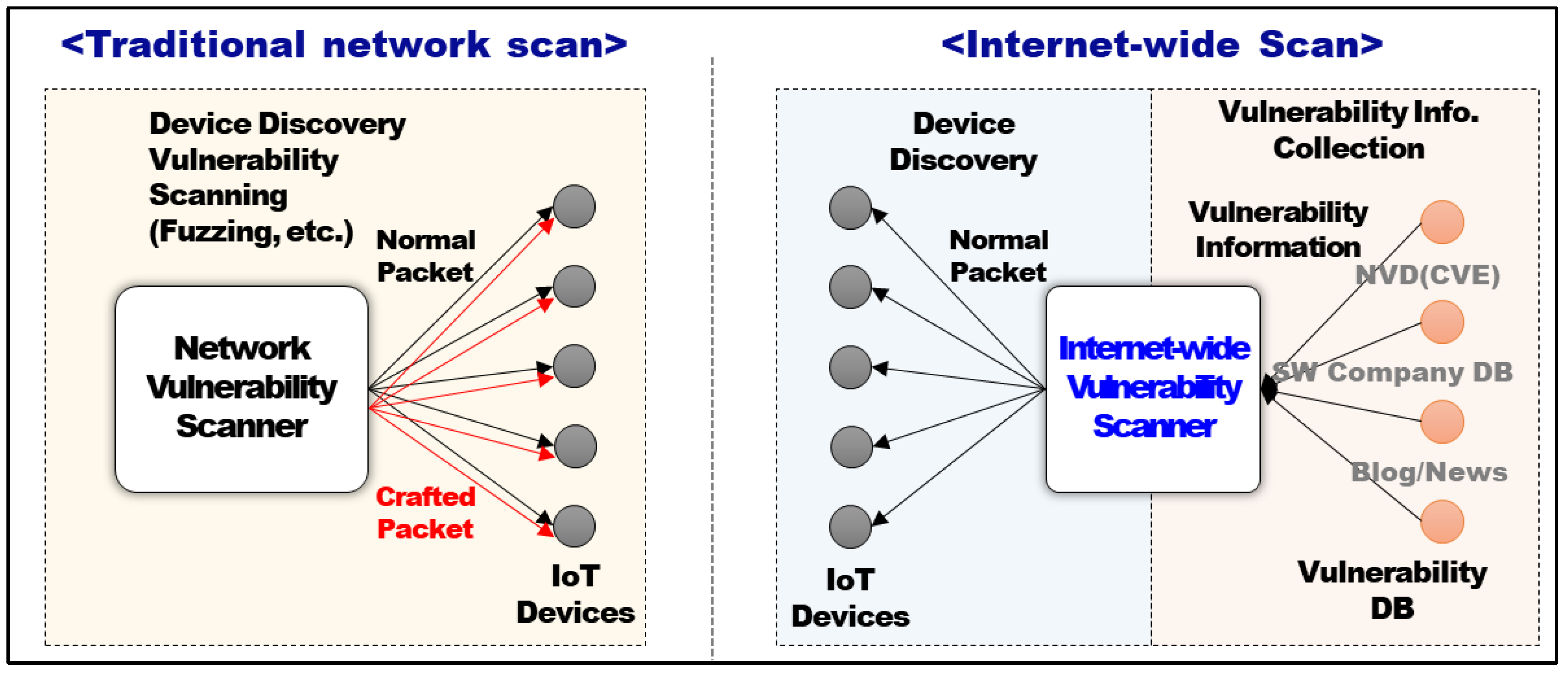
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices
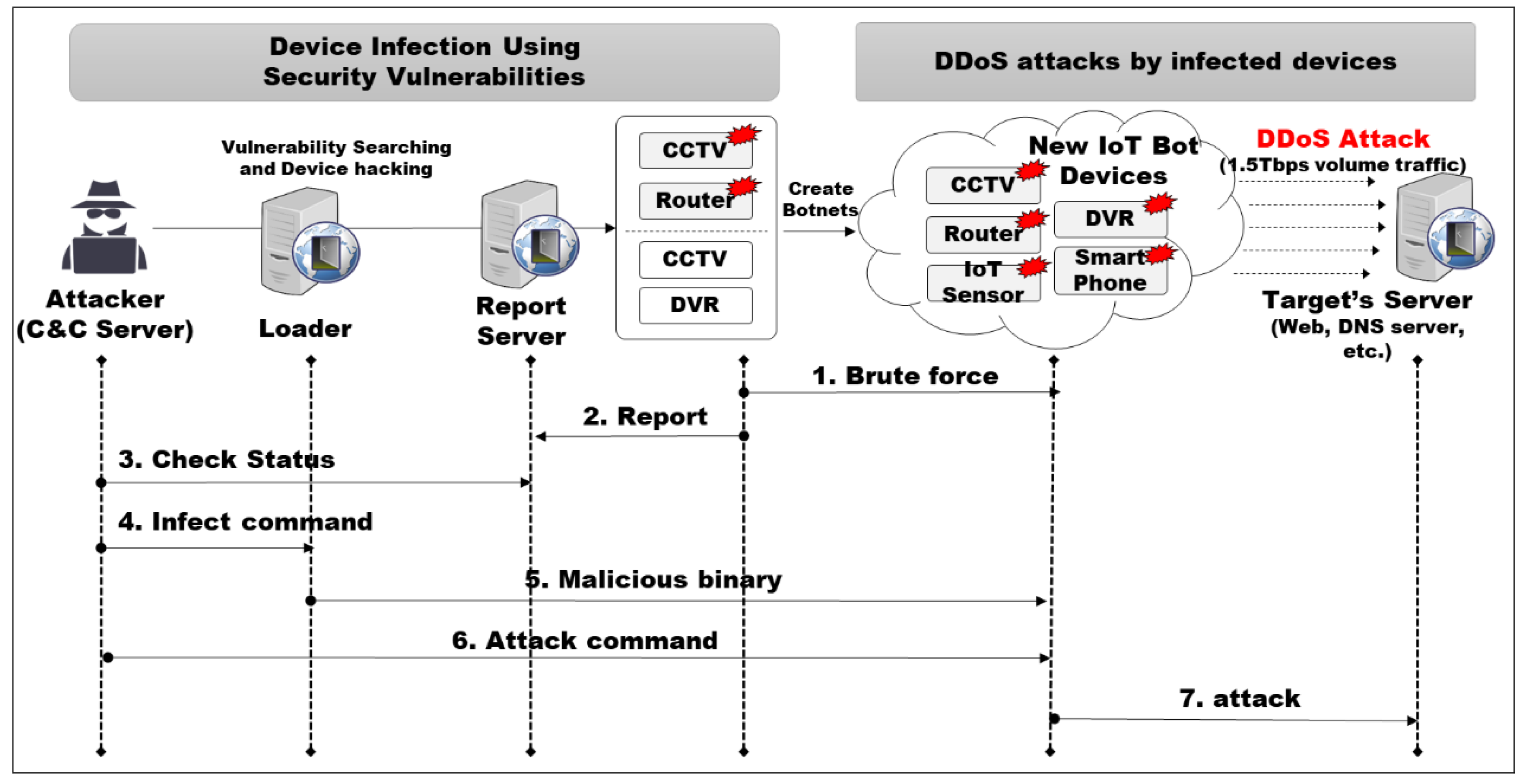
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices

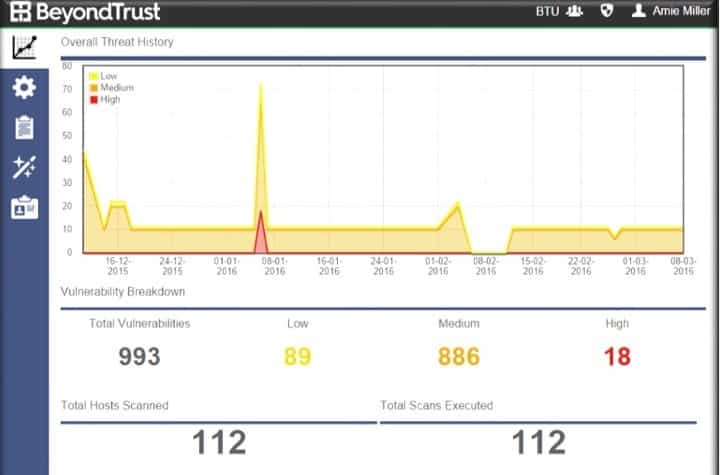
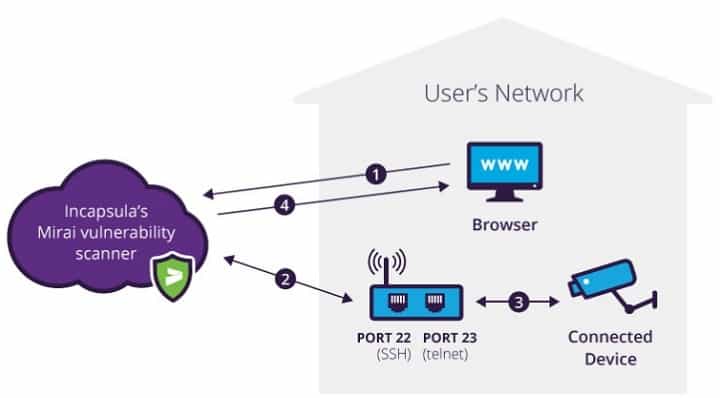
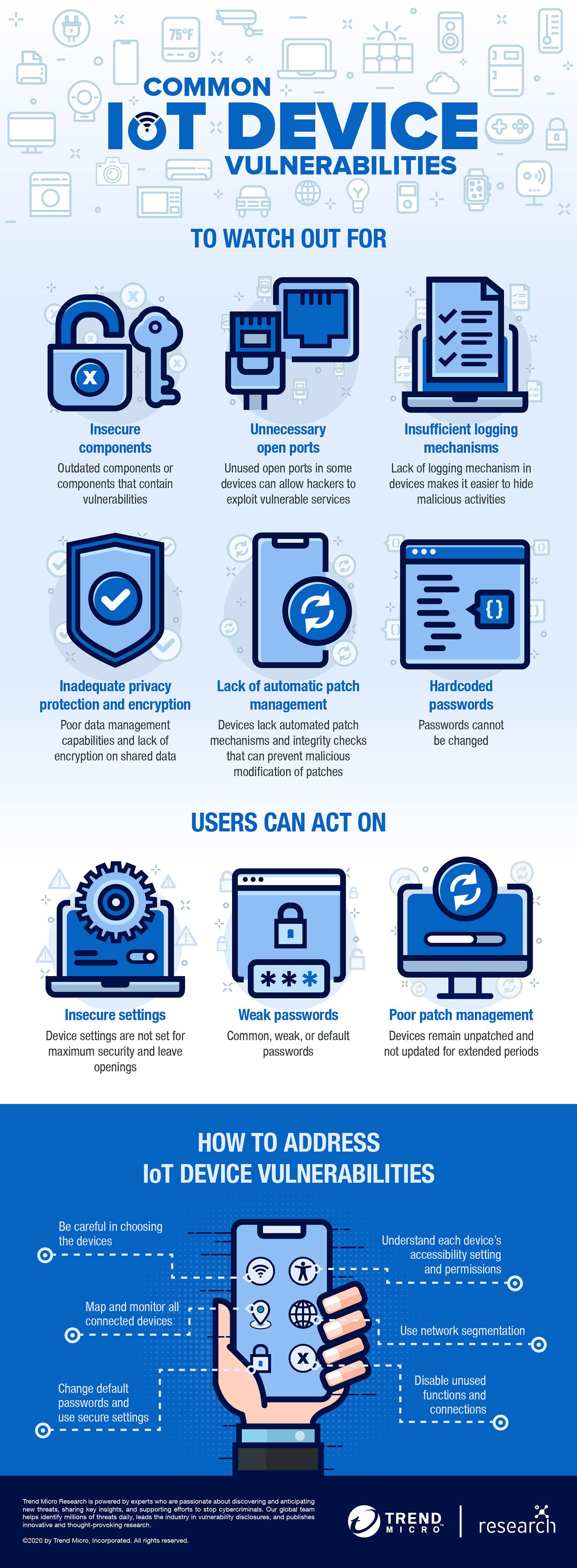




![Top 5 IoT vulnerability exploits in the smart home [list] Top 5 IoT vulnerability exploits in the smart home [list]](https://www.minim.com/hubfs/iot-vulns-feature-12.jpg)